
Request For Products: What To Build On Arcium
Arcium is the encrypted supercomputer — encrypted shared state, composable with public chains, built for apps that simply can’t exist on transparent ledgers.
With the recent launch of Phase 2 of the Arcium Public Testnet, we are highlighting a set of applications with strong market demand and clear revenue potential. These have been prioritized based on the size of the opportunity, ease of adoption, and the ability to unlock entirely new business categories.
We begin by outlining applications where Arcium powers the core product itself, followed by use cases where Arcium enhances specific components of broader applications.
DeFi
Dark Pools / Private Trading
Dark pools are private trading venues where participants can place orders without revealing details until after execution. In traditional finance, 40–60% of US equity trading volume runs through dark pools, yet none exist on Solana today — a clear market gap.
In DeFi, this matters because full transparency is a double-edged sword: while it enables trustlessness, it also exposes traders to MEV attacks, front-running, and price slippage. As a result, serious traders are often forced back to centralized exchanges instead of staying onchain.
Arcium fixes this by running matching and risk logic inside encrypted shared state. Orders and balances remain hidden, execution is private, and settlement is only revealed once it is safe. Counterparties cannot see each other and MEV cannot intercept the flow. This makes large-scale trading viable onchain, unlocking institutional demand and fee generation from day one.
Prediction, Opinion, and Opportunity Markets
Prediction, opinion, and opportunity markets all try to surface information that institutions normally struggle to access — but each does it in a different way.
Prediction markets aggregate beliefs about real-world events. They resolve against an external truth (elections, sports results, economic data). One of their biggest challenge is resolution integrity: when settlement votes or oracle inputs are visible, whales or coordinated groups can tilt outcomes. The Zelensky “suit” market on UMA is a good example — the market initially resolved “yes,” but was later flipped to “no” after dispute votes dominated by large tokenholders.
Opinion markets have no external truth. The outcome is the collective opinion. If votes are public in real time, participants herd toward the majority instead of expressing their true beliefs, collapsing the diversity of input that gives the market value. Using a commit–reveal mechanism helps prevent this by hiding votes until the reveal phase, forcing participants to submit their actual view rather than anchor on visible majorities.
Opportunity markets unlock information about things that institutions could act on, but that only outsiders discover first (unsigned artists, startups, overlooked research, emerging trends). Instead of relying on adversarial counterparties (like prediction markets) or public voting (like opinion markets), opportunity markets create private prediction environments where only the sponsor sees prices. Scouts bet on opportunities, the sponsor pays when they act on them, and prices/positions are only revealed after an “opportunity window.” This lets institutions tap into global scouting without leaking alpha to competitors.
Arcium enables encrypted market design that makes these mechanisms possible.
Private Perpetuals
Perpetual futures dominate crypto trading volumes, yet onchain perps remain exposed. Public orderbooks reveal positions and strategies, making traders vulnerable to copy-trading, front-running, and targeted liquidations — as seen in the James Wynn incident. This risk drives serious traders back to centralized exchanges.
Arcium enables encrypted perpetuals where intent and execution remain private, and details are only revealed once a position is closed. This prevents exploitation, creates a safer environment for larger liquidity providers, and supports deeper markets with more efficient price discovery.
Private Lending & Borrowing
Onchain lending protocols publicly reveal collateral, borrow amounts, and liquidation thresholds. This transparency allows third parties to track positions and increases the risk of targeted liquidations. With Arcium, interest calculations, loan-to-value ratios, and liquidation checks can be performed inside encrypted state, so user health factors remain private while the protocol still enforces solvency.
C-SPL can also be used to wrap assets such as USDC into confidential versions, ensuring that loan amounts and repayments are hidden onchain while preserving full composability with DeFi.
Blind Auctions
Blind auctions are mechanisms where bidders cannot see each other’s offers until the auction ends. The most common form is the sealed-bid auction, where participants submit confidential bids and only the outcome is revealed after closure. This structure prevents bidders from gaming the process by reacting to others, ensuring fairer competition.
Sealed-bid formats dominate many high-value markets: government procurement, spectrum licenses, real estate foreclosures, and even government bond sales. Depending on the design, winners may pay their own bid (first-price), the second-highest bid (Vickrey), or a uniform clearing price (as in some securities auctions). Across these domains, sealed-bid auctions account for hundreds of billions of dollars annually.
Onchain, by contrast, auctions are transparent by default — bids appear in real time, creating opportunities for collusion, MEV extraction, and last-minute sniping. Arcium enables blind auctions onchain by encrypting all bids inside shared state and only revealing the results once the auction ends. This unlocks truly private, fair price discovery and broadens DeFi’s auction design space, from institutional-scale bond sales to consumer-facing marketplaces and NFT drops.
Confidential DAO Treasury
Corporate treasuries and foundation funds depend on confidentiality around balances, allocations, and spending decisions to protect strategy and maintain discretion.
DAO treasuries onchain reveal exact holdings and transactions, creating competitive disadvantages and discouraging contributors who value financial privacy.
With Arcium and C-SPL, DAO treasuries can keep asset amounts and spending confidential while governance approvals and accountability remain transparent. This protects sensitive financial data without sacrificing community oversight or programmable fund management.
Private Voting (DAO Governance)
Private voting on Solana with Arcium works by keeping every vote hidden until the final tally is revealed. Instead of recording votes directly onchain where anyone can see them, Arcium collects and processes them privately. The network only releases the final result together with a proof that it was counted correctly, so voters remain anonymous while the outcome stays trustworthy and verifiable on Solana.
Gaming
Hidden-Information Games
Strategy games onchain don’t work because transparency kills the game. With Arcium, unit positions, hidden moves, and private inventories live in encrypted state; only the minimal reveal escapes at resolution steps. It won’t print dark-pool fees, but it will own mindshare. This is the “see it to believe it” demo that proves Arcium runs fair logic without leaking the board.
Onchain games today are unplayable because full transparency kills the mechanics. Hidden-information games rely on secrecy — whether it’s private hands, secret inventories, or hidden player locations. With Arcium, these hidden states live securely in encrypted shared state and are only revealed when the rules require it. This unlocks entire categories of gameplay that public blockchains currently make impossible.
Classic private-hand games like Poker, Blackjack and other casino classics depend on cards that only the player can see. Fog-of-war strategy games such as Dark Forest or mainstream titles like StarCraft rely on hidden maps, troop movements, and scouting. Modern FPS and battle royale games like Fortnite and CS:GO combine both: you can’t see every player’s location on the map, and you also can’t know their loadout until it’s revealed in combat. Even RPGs and loot-based games (think Diablo or Zelda) depend on secret inventories that only surface when used or traded. Arcium makes all of these models viable onchain, proving that full game logic can run privately and fairly without leaking the board.
Other Classes of Games
Beyond hidden-information play, transparency also breaks entire genres built on secrecy. With Arcium, these mechanics become viable onchain:
- Guessing Games
- Hangman
- Wordle
- Sudoku
- Geoguessr
→ collapse because the answer is visible from the start.
- Social Deduction & Bluffing Games
- Mafia
- Werewolf
- Among Us
→ lose meaning once hidden roles are exposed.
- Randomness-Dependent Games
- Yahtzee
- Collectible card games
- Lotteries
- Raffles
→ fail if dice rolls, deck draws, or ticket counts are public.
- Asymmetric Information Strategy Games
- Battleship
- Mastermind
- Stratego
→ fall apart when secret positions or piece identities can be read from the ledger.
Randomness
Many game types also fail onchain because randomness isn’t truly random. Public RNG systems leak entropy, can be front-run, or let sequencers bias outcomes. Cryptographically secure randomness (CSPRNG) fixes this by generating unpredictable values that no one can manipulate or anticipate.
With Arcium, dice rolls, card shuffles, loot drops, spawns, and crit chances — all the randomness that defines modern gameplay — can be generated privately and securely. This unlocks fair versions of everything from collectible card games to roguelikes to battle royales, where uncertainty is a core mechanic.
Miscellaneous
Universal Private Biometric Login (Server-Side)
Today, biometric authentication on iPhones and MacBooks relies on Trusted Execution Environments (TEEs) such as Apple’s Secure Enclave. Fingerprint, Face ID, and Touch ID templates are stored and matched locally, powering hundreds of millions of devices worldwide. While this is secure, it is limited: each vendor’s TEE only works within its own hardware ecosystem, creating a fragmented, device-bound approach.
Arcium enables a universal model for biometric authentication that is not tied to proprietary hardware. Biometric templates are stored as encrypted shares rather than raw data, and match scores are computed privately inside encrypted shared state. Applications receive only a yes/no response plus proof, never the underlying biometric information. Unlike Apple’s local TEEs, this universal approach works across devices, platforms, and vendors, offering portability, vendor independence, and stronger privacy guarantees. It is a UX unlock that requires ecosystem coordination — feasible, valuable, but not the first GTM.
Encrypted DNA Matching
DNA can reveal ancestry, health traits, and family connections, but today services like 23andMe require storing raw genomes on centralized servers to do this. They compare your DNA markers against millions of others in their database, which lets them estimate ancestry percentages or identify relatives. The tradeoff is enormous: you get useful results, but a company ends up holding one of the most sensitive datasets imaginable — your entire genetic code.
Encrypted DNA matching changes that. Instead of exposing raw genomes, both your DNA and the reference databases stay encrypted, and only the comparison results are revealed. That means you could still discover you’re “70% Norwegian” or that you share DNA with a likely cousin — but no one, not even the platform, ever sees your underlying genetic sequence. It unlocks huge social and medical value while sharply reducing the privacy risks, though regulatory friction means adoption will lag behind less sensitive applications.
Onchain Social Media
Another sector that becomes possible with Arcium is onchain social media. Public social graphs and user data create a massive privacy breach that most users would never accept. While some projects rely on offchain storage with occasional onchain elements, this breaks composability and limits the ability to build fully interoperable social applications.
Arcium solves this by keeping social graphs, profiles, and interactions encrypted in shared state while still allowing composable access through permissioned policies. This means friends lists, messages, and user relationships can stay private, while applications can still interoperate on the same encrypted layer. Onchain social built this way preserves user privacy while unlocking the network effects and composability that make Web3 powerful.
Privacy Features for Products (Not full apps)
Threshold Signing
With threshold signing, the private key is never reconstructed in one place. Instead, pieces of it are split across Arcium’s MPC network, and only when a defined threshold of parties come together can a valid signature be produced. No single node, app, or AI agent ever has unilateral control.
Take the same DeFi + AI agent example. You type “go long 2x on SOL,” the agent prepares the transaction, and the signature gets generated collectively across Arcium’s MPC nodes. The AI doesn’t hold your key, you don’t hand it over, and there’s no single point of failure. You remain in control by setting policies — maybe the agent plus you plus a quorum of Arcium nodes must all participate before the signature is valid.
That means an AI agent can act on your behalf without ever compromising your private key, unlocking safe autonomous execution where trust is distributed instead of concentrated.
Private Data Transfer & Access Control
This is “cryptographic ACLs” — think Dropbox or Google Drive, but with no trusted server. The storage can sit anywhere (S3, IPFS, Arweave), while the keys, policies, and metering all live inside Arcium’s encrypted shared state. Arcium enforces who can decrypt what, when, and under what license or paid policy — without leaking the ACL itself.
Example: a company shares an encrypted dataset with multiple partners. Instead of trusting a central server, each partner’s decryption rights are enforced by Arcium. Access can expire after a week, unlock only after payment, or meter by usage — all enforced cryptographically. Once embedded, this becomes sticky B2B infrastructure for data licensing, SaaS distribution, and enterprise file sharing.
Private Subscriptions
Where access control is about objects, subscriptions are about relationships. A private subscription keeps the subscription state encrypted onchain, with Arcium enforcing who is subscribed, which tier they’re on, and whether payment is current. Payments use confidential transfers to hide amounts and counterparties, while user-owned protocol accounts maintain and update subscription state privately.
Example: a DeFi app offers a premium strategy tier. Users pay recurring confidential transfers, and the subscription state is updated inside Arcium. The app checks the state to grant access, but no one can see who subscribed, how long they’ve been active, or what they’re paying. It’s Stripe or Patreon rebuilt as an encrypted primitive, giving creators and apps subscriptions without surveillance.
Private Contact Discovery
Most wallets and social apps need network effects — they become more valuable when you can easily find friends or contacts already using them. The problem is that traditional contact discovery requires uploading your whole address book or follower list, which leaks sensitive information about people who never signed up.
With Arcium, this can be done privately. Using encrypted set intersection, the system compares your contacts with the app’s user base without revealing the full list. You only learn about the matches, and the non-matches stay hidden. This makes onboarding smoother and helps build trust, since users don’t have to sacrifice their contacts to start connecting. It’s an important feature for growth, but not an entire product in itself.
Confidential Messaging & Email
The market is crowded and distribution is the real problem. If you’re already building comms into a product, Arcium gives you onchain E2E with policy-based access and archival proofs. As a standalone, it’s uphill; as an embedded feature, it’s sticky.
Anonymous Confessions & Confidential Matchmaking
Fun, viral, and great for showing off encrypted matching and eligibility proofs. On Arcium, membership can be verified and preferences matched without exposing identities or embeddings. Expect mindshare, not mountains of revenue.
Confidential Password Storage With Recovery
MPC-backed vaults with programmable recovery policies. Arcium holds the shards and enforces the policy logic privately. It’s a credible demo and a solid feature for wallets; hard to win standalone against incumbents.
C-SPL Applications
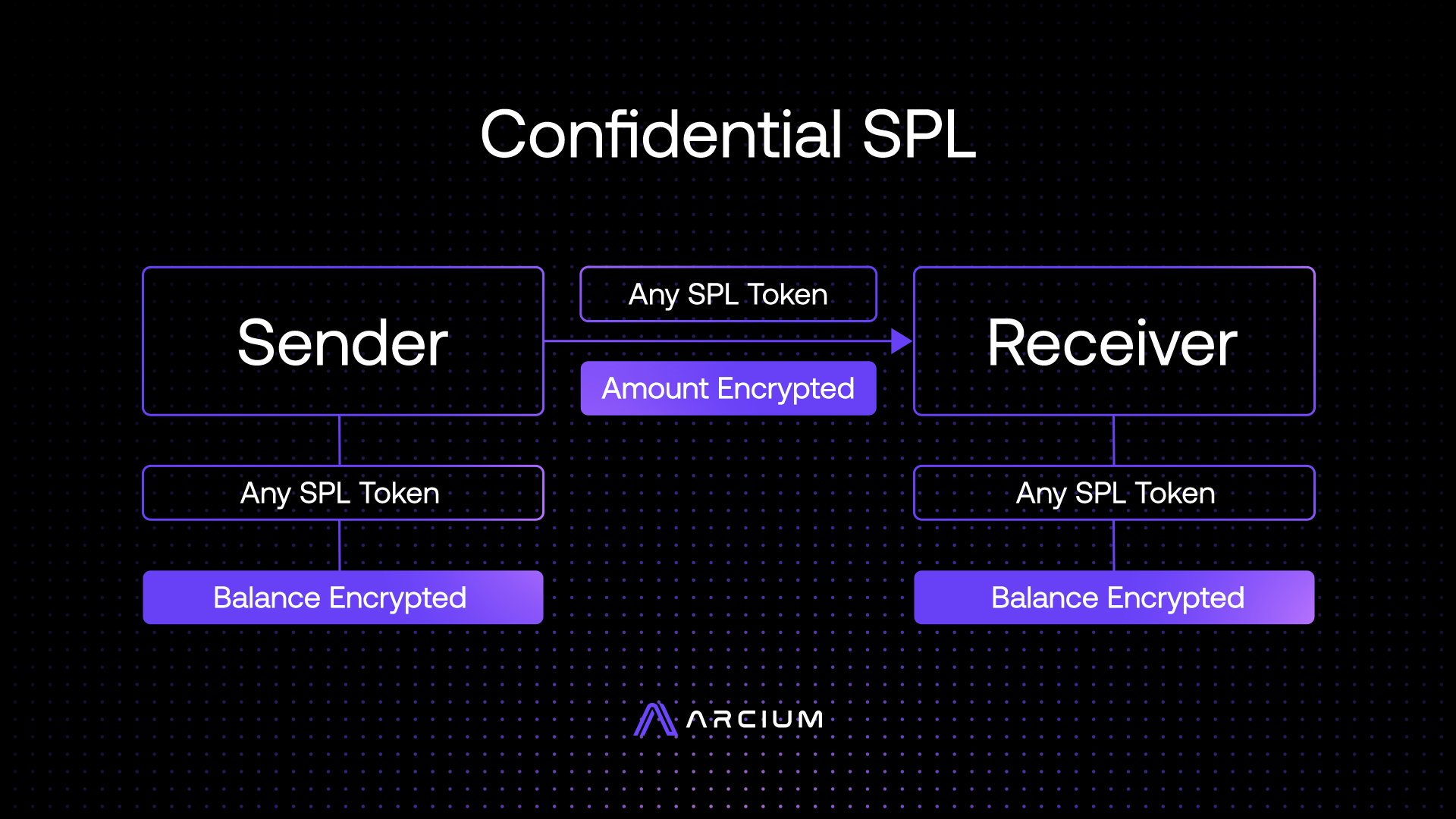
Programs can enable C-SPL as well, to really simplify confidentiality in applications.
Confidential Lending / Borrowing (nobody can see how much you lend/borrow), confidential perps (outsiders can’t see the amount you’re trading, but they can see when you enter / exit), same with trading
Confidential Onchain Retail and Shopping
Stablecoins are rapidly gaining adoption and it makes sense to use them for everyday retail payments. The challenge is that onchain transactions are fully transparent, exposing balances and spending habits to anyone watching.
Arcium and C-SPL solve this by allowing anyone to wrap an existing stablecoin like USDC into a confidential version and pay with it directly. Balances and transaction amounts remain encrypted onchain, protecting consumers from surveillance, unwanted exposure, and predatory marketing while enabling seamless private payments anywhere stablecoins are accepted.
Onchain Salary and Compensation
Payroll today runs on outdated infrastructure, with cross-border salaries moving through fragmented providers that create delays and high fees. Stablecoins fix much of this by enabling instant settlement and letting companies operate from a single pool of liquidity instead of juggling multiple accounts and currencies.
Arcium and C-SPL extend this by making payroll private. Any stablecoin, like USDC, can be wrapped into a confidential version and paid out directly to employees. Balances, amounts, and dates stay encrypted onchain.
This gives companies and workers the efficiency of onchain payroll without exposing sensitive compensation data, keeping salaries secure from public view and unwanted tracking.
Artificial intelligence / Machine Learning
Arcium’s AI-optimized protocol, Manticore, will launch shortly after Mainnet. Originally acquired from Inpher and further developed by the Arcium team, Manticore unlocks a new generation of privacy-preserving AI applications, enabling use cases such as:
Encrypted RAG
RAG (Retrieval-Augmented Generation) is basically AI with a memory it can search through. Instead of relying only on what a model was trained on, it can look things up in an external knowledge base (like documents, notes, or databases), pull back the most relevant pieces, and then use those as context when answering.
Normally, when you do RAG, the system sees both your query and the documents it’s searching. With Confidential RAG on Arcium, both the stored data and the search query stay encrypted. The network can still figure out which document is most similar (using cosine similarity) without ever seeing the raw text. Then only you decrypt the result.
Example:
Imagine a hospital with a huge archive of patient records. Doctors want to query this data to find cases similar to their current patient. With normal RAG, the system running the search could see both the query and the records. With Confidential RAG, the hospital can run these searches without exposing private patient data to anyone — not even the network doing the computation.
Encrypted AI Training
AI models are only as good as the data they’re trained on, but most valuable datasets (medical, financial, corporate) are highly sensitive. Arcium allows multiple parties to train a model directly on encrypted data, ensuring that no one sees the raw inputs. A pharmaceutical company, for example, could train models on genomic data without ever exposing patient DNA sequences, preserving privacy while still extracting value.
Collaborative Encrypted AI Training
When multiple institutions want to jointly train an AI model but cannot share data directly, Arcium enables them to contribute encrypted datasets to a shared training process. Each participant’s data remains private, but the model benefits from the combined knowledge. A concrete example would be several banks training a fraud detection model together — learning from broader patterns while keeping each bank’s customer data confidential.
ML Predictions
Machine learning predictions often require sending data to a model hosted on external servers, which risks exposing sensitive inputs. With Arcium, a user can submit encrypted data for prediction, and the model’s output is also encrypted until the user decrypts it locally. This enables scenarios like confidential medical test results being analyzed by a model without revealing patient inputs or outcomes to the service provider.
Encrypted AI Inferencing on SLM’s (Small Language Models)
Small Language Models (SLMs) are lightweight AI models optimized for specific tasks. Arcium makes it possible to run inference on encrypted inputs, so organizations can deploy SLMs without ever seeing user data. For example, a finance firm could offer an encrypted chatbot trained to analyze client portfolios — customers ask private questions, the model runs on encrypted inputs, and only the client sees the decrypted answer.
Feel free to reach out to discuss your AI application and explore how Arcium can integrate to enhance its capabilities.
The Takeaway
If you want to generate meaningful traction now, build where transparency has become a constraint and privacy is the unlock. Focus on areas where encrypted computation creates new market advantages — where privacy isn’t a feature, but the foundation for revenue and defensibility.
If your goal is visibility and influence, create something that captures mindshare — a flagship application that showcases what’s possible with encrypted compute, fully onchain and verifiable. And if you’re thinking longer term, the path into enterprise will run through encrypted systems that balance privacy, verifiability, and compliance.
Arcium provides the flexibility to grow in any of these directions. Applications can start simple and expand over time, adding new functionality as your project grows. Every app built on Arcium is inherently chain-agnostic: while we’re launching first on Solana, all applications will remain compatible as the network extends to Ethereum and beyond.
We maintain an example repository that is continuously updated with code examples for different applications built with Arcium. It acts as a directory of use cases and reference implementations, showing how these applications can be built and extended. A great starting point for developers: https://github.com/arcium-hq/examples
Reminder: the Colosseum Cypherpunk Hackathon is now ongoing — and Arcium is sponsoring both the DeFi Track on Colosseum and the newly launched <encrypted> Side Track on Superteam .
Build with encrypted compute, unlock new on-chain design space, and compete for $75K in total prizes — including $55K for the DeFi Track and $20K for the <encrypted> Side Track and hands-on support from the Arcium team.
See you in the arena.
.svg)










.svg)




.svg)























.jpg)





.jpg)

